So you’ve taken pains to hide your WordPress login and admin screens from hackers. You’ve changed your default usernames and removed all mention of them from your theme. You’re safe right? There’s no way that hackers can find your login pages, let alone your usernames. Wrong! Unless you take precautions, here’s how hackers can find your WordPress username with ease. And not just yours – those of everyone on the site.
Two Methods:
Method 1: Using /?author=1 Query Parameter
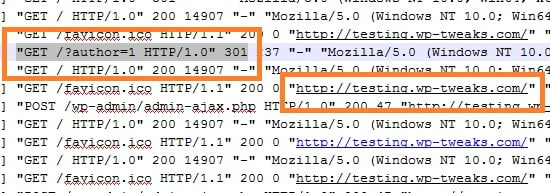
One day, I had just set up a new blog and thought I’d hidden my admin areas pretty well. To my surprise, my security plugins started sending me lockout notices. This means that not only were hackers able to find my login page, they were able to guess my WordPress username as well! I opened up my raw access logs in cPanel, and found this:
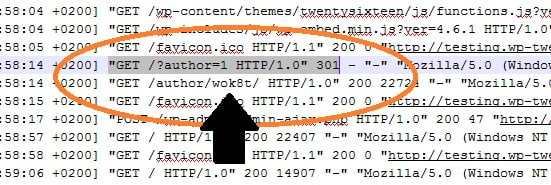
Apparently, hackers can find your username in WordPress by appending the query /?author=1! You can see in the screenshot above that my server immediately returned the author page, revealing the username. So forget about making your username difficult to guess. It’s right out there in the open!
Here’s how it looks. First, type in your blog name and type /?author=1 after the URL like this:
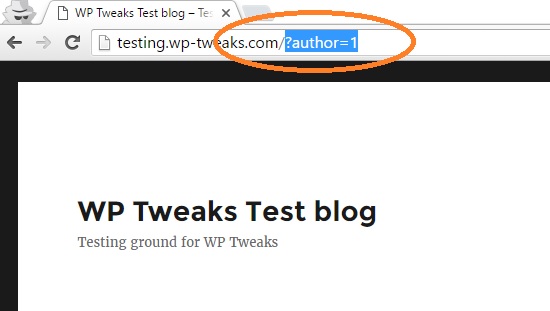
This will immediately redirect to your author page like so:
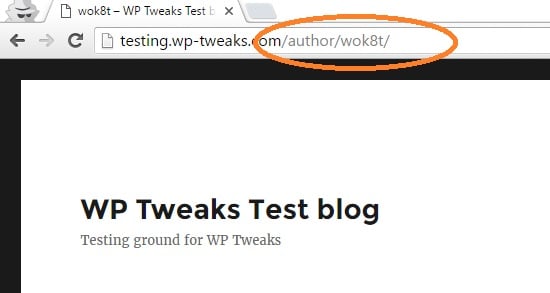
Some experts claim that exposing WordPress usernames is not a security risk. According to them, creating a strong password and using two-factor authentication is the right way to go about it. But I say there’s nothing wrong with hiding as much information as possible from hackers. Maybe if someone is truly determined to know my username, they can. But that doesn’t mean I have to make it easy for them! I want potential attackers to work to break into my site. Hopefully, this will deter 90% of them.
If hackers don’t know your username, they won’t spam your site, trying to guess your password. This means less load on your server. I’ve been brought down once before by hackers DDoS’ing my login page, and I don’t want to risk that again.
So how do we close this loophole? There are two ways to prevent WordPress from revealing your author name via the parameter hack.
Fix 1: Modifying .htaccess
This is my preferred technique because it’s much faster than the alternative. By creating a simple .htaccess rule, you can immediately block all attempts to access your WordPress username via the ?author parameter. If you have access to it, open the hidden “.htacces” file in the root directory of your WordPress installation, and paste in the following code at the end:
RewriteEngine On
RewriteCond %{REQUEST_URI} !^/wp-admin [NC]
RewriteCond %{QUERY_STRING} author=\d
RewriteRule ^ /? [L,R=301]Here’s what the WordPress .htaccess looks with the above code added on:
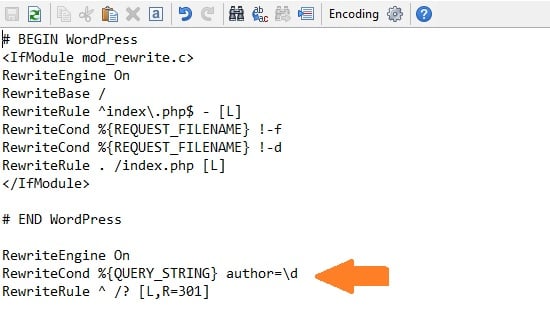
These rules check if you’re in the admin area and whether or not someone is attempting to access the “author” query parameter. If the conditions are met, it redirects back to the WordPress homepage. Problem solved!
After implementing this code in my .htaccess, the raw access log entry looks like this:
So even though someone has attempted to find my username by typing “/?author=1”, the server smartly sends back my blog’s homepage. This is an extremely fast process and hardly uses any server resources. So it’s the efficient and preferred way.
But what if you can’t make changes to .htaccess? Then the second method is the one for you.
Fix 2: Adding a Code Snippet to WordPress
The second method is to add a code snippet to WordPress that accomplishes the same. If you don’t know how, read my earlier step-by-step tutorial on how to do this. Here is the code you need to paste into your custom plugin or functions.php:
function redirect_to_home_if_author_parameter() {
$is_author_set = get_query_var( 'author', '' );
if ( $is_author_set != '' && !is_admin()) {
wp_redirect( home_url(), 301 );
exit;
}
}
add_action( 'template_redirect', 'redirect_to_home_if_author_parameter' );
Like the .htaccess code, this does exactly the same thing. It checks to see if you’re not in the admin area, and whether or not someone is trying to access the author name via the “?author” parameter. If so, it redirects back to the home page.
The difference is that this executes at the WordPress level and is slightly more inefficient than the first method. But if you don’t have access to .htaccess, it’s the only other way. Checking your access logs will reveal the same regardless of your chosen method.
So while some might deny that revealing usernames is a security threat, my principle is that the harder you make it for someone to snoop around your website, the better. And if you want to prevent brute force attacks and hackers from finding your WordPress username, one of these two code snippets will do the trick!
If you’re looking at really getting the most out of WordPress, you should consider specialized hosting. Different companies have different deals, and you can view the comparisons of WordPress hosting prices at one glance.
Fix 3: Use Cloudflare Page or Firewall Rules
Many websites use Cloudflare anyway, so this is an easy solution. Add a new page or firewall rule to exclude the problematic URL. You can redirect the page to the home page or block it altogether. The free version of Cloudflare comes with three free page rules and three free firewall rules that you’re probably not using. So we might as well utilize them!
Method 2: Using WordPress JSON REST Endpoints
Visit the following URL on your WordPress site:
https://[yoursite]/wp-json/wp/v2/users/1
Replace [yoursite] with your site name. You should get something like this:
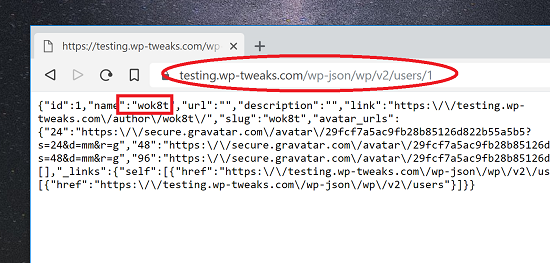
That’s your WordPress username in plain sight! This is because WordPress exposes certain REST APIs by default, allowing anyone to enumerate the users via JSON.
Fix: Disable via Code
Fortunately, we can just disable these endpoints via this simple code snippet:
function disable_rest_endpoints ( $endpoints ) {
if ( isset( $endpoints['/wp/v2/users'] ) ) {
unset( $endpoints['/wp/v2/users'] );
}
if ( isset( $endpoints['/wp/v2/users/(?P<id>[\d]+)'] ) ) {
unset( $endpoints['/wp/v2/users/(?P<id>[\d]+)'] );
}
return $endpoints;
}
add_filter( 'rest_endpoints', 'disable_rest_endpoints');
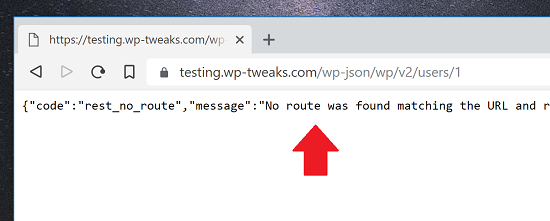
After you’ve saved your changes, your server will send users this message instead:
Fix 2: Disable JSON via Cloudflare Firewall Rules
Instead of blocking JSON using WordPress code, I find it easier to block it with Cloudflare. That way, your site doesn’t bear the burden of processing possibly thousands of spurious requests. You can use Cloudflare’s firewall rules to achieve this, as shown here:
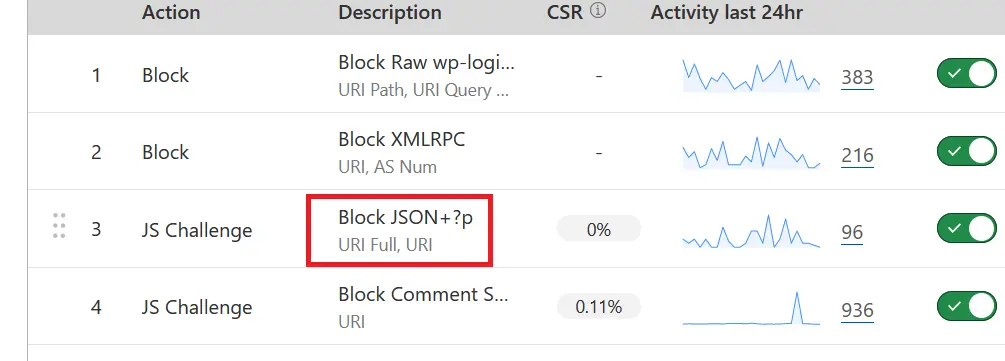
To create this rule, I use the pattern “URL Full” contains /wp-json:
(http.request.full_uri contains "/wp-json")
And I set the action to “JS challenge” instead of “Block”. But be careful. When Cloudflare blocks REST API requests, it can cause WordPress Gutenberg to malfunction and the Jetpack plugin to disconnect. I don’t use Jetpack, so it doesn’t affect me, but you might want to disable the JSON blocking rule when editing a post in WordPress.
Blocking these two methods should make it hard for hackers to access your username!

Thank you for writing about this topic. I think I might have found another option:
Install the plugin “Edit Author Slug”, then enter a new author slug (different to your username) in your profile. You can also set a 301 Redirect from the old version to the new one by entering the following in .htaccess :
RewriteEngine On
Redirect 301 /author/username-that-you-want-hidden/ http://example.com/author/new-name/
With this method, the author’s archive page is still usable.
In place of installing third part plugin and lots of code which you might not aware, you can use just hook which is provided by @Bhagwad Park
This is much better approach rather than rely on another plugin and main there updates and so on….
I agree the solutions suggested are much better than installing a third party plug-in which is a vulnerability in itself. Thanks for this article. It is a shame that we have to concentrate on security as much as we do.
Thanks for that!!! So many and “little” things you have to think about
Very informative information thanks for sharing with us.
Hey! I now thks is somewhat off topic but I was wondering if you knew where I could find a casptcha plugin for
myy coomment form? I’m using the same bloog platform as yours and I’m having
difficulty finding one? Thanks a lot!
Thanks for this, great solution . I was searching for a solution because I have several hacking attempts doing exactly this. .htaccess solution worked a treat I really wanted to do this server side. 🙂
Did not work for me at all. Could the other plugin be interfering?
Here is what htaccess looks like after the WordPress.
…………………
# END WordPress
# BEGIN DS-XML-RPC-API
# The directives (lines) between “BEGIN DS-XML-RPC-API” and “END DS-XML-RPC-API” are
# dynamically generated, and should only be modified via WordPress filters.
# Any changes to the directives between these markers will be overwritten.
order deny,allow
deny from all
# END DS-XML-RPC-API
RewriteEngine On
RewriteCond %{REQUEST_URI} !^/wp-admin [NC]
RewriteCond %{QUERY_STRING} author=\d
RewriteRule ^ /? [L,R=301]
hi,
as third attempt its possible to use the “author.php” and put just the redirect code in.
that way when have to add author profile pages later on it will be easy to find and replace.
Perhaps a stupid question, but does it matter if that piece of code (or any piece of code?) for the .htaccess is inside or outside of the tags?
example: If I append that BEFORE the will it still work?
I think it should still work. Let me know if it doesn’t!
Yikes! There’s a vulnerability I hadn’t thought of! Especially when combined with the xmlrpc.prg file that allows multiple requests per request. Say, a xmlpc.prg that has parameters to try a rainbow table of passwords to login. And then continual login attempts…
Yikes again!
This is going in all the sites I manage right now! (And is why there is a phony email address in this comment – I need some time to get this on all my sites.)
Glad you found it useful!
This is a great tweak, thanks!
I use wordfence on all the websites that I maintain and on every unsuccessful login attempt it fires off an email to me and blocks the ip of the user for 4hrs. I bet you can guess how many emails I get just from this alone!
This tweak should make it much more interesting for these ‘users’.
Glad you found it useful! I’ve just discovered another method to find the username and will be updating the article to reflect this soon!
In case anyone stumbles on this you can turn off the Wordfence emails that are informational instead of actionable. You can even limit how many emails Wordfence sends in an hour (caution – 0 means unlimited!)
See this helpful video to learn more
https://youtu.be/d50knnGXNO4
– Mia
I have started to get notifications recently that hackers are able to figure out my username. Before, they try to login with Admin or other similar usernames, but now they are able to guess the exact username few minutes after I change it. I tried your method but my website returns a 404 page when you add /?author=1 to the URL.
So my question, is there another way hackers can figure out my username?
I recently found another way to get the author name. I’ll update this post it in a couple of days. Check back soon!
I added the `?author=1` after my Blog’s URL, and didn’t get the Author name. Does that necessarily mean that my site is protected from this, or maybe I’m missing something…?
What page do you get when you type it in? A 404?
If you use Anti-Malware from GOTMLS.NET plugin, it automatically blocks that query.
I checked both of your methods and found that my site was vulnerable to both. Fixed it with your solutions, now working properly and without the vulnerabilities. Thanks!
Hello, for Method 2: (Using WordPress JSON REST Endpoints)
Where exactly do we add this code snippet ?
Thank you
You should use a custom plugin for snippets like this: https://www.wp-tweaks.com/create-wordpress-custom-plugin-code/
Thanks man. Really appreciated. I was going nuts. My site was online for about an hour when the attacks started and I was flabbergasted that they knew my admin name (which, clearly, wasn’t Admin). I couldn’t get it to work with the custom plugin (the edit button didn’t appear, even with all plugins deactivated) but I am now using the Code Snippets plugin…
Hey,
Neither method one or method two shows my username, in method two I this: {“code”:”rest_user_invalid_id”,”message”:”Invalid user ID.”,”data”:{“status”:404}}’.
People are still able to guess my username though, how? (my site isn’t even live!)
Keep on increasing the number and you will get a result sooner or later.
what do you mean by ”keep increasing the number?”
I believe this person is referring to the fact that you can increment the 1 in this /?author=1 to search for results – 1 denotes a userID and that does not mean that another userID will not return a result
Hi!
I added the below code to the .htaccess file in the WordPress root folder, but it didn’t help out. Still able to the the /?author=1 and it responded with the user name.
RewriteEngine On
RewriteCond %{REQUEST_URI} !^/wp-admin [NC]
RewriteCond %{QUERY_STRING} author=\d
RewriteRule ^ /? [L,R=301]
Remove the second line then it worked for me. Some say about using the author.php how do they use that? Can someone show an example of fixing that way please. Thanks
Thank you very much. It was very annoying to see unauthorized login attempts a few hours after I did reset my admin username and password – again! This is not even covered by many security suite plugins, that are overly bloated, as far as could test them.
Cheers, corumeach
I think you should add the redirect also to the author permalink otherwise a hacker can still access the author page and try and guess a login name. A valid user will return a 200 response and invalid 404.
eg https://example.com/author/admin/ will return a 200 response if the username exists.
Thanks for the idea! Are you sure about this? If you post a test URL, I can evaluate the response headers and see how to proceed further…
I put in his code and it got me to a page with some unedited page on my site but with a 404 below that. However, hitting any menu item took me to the maintenance screen (which is correct for now)
Keeping this topic running, ..
Gobsmacked to see that https://[your website]/?author=1! showed my login username.
From it: I simply can’t believe that the <> haven’t been using it, but they haven’t, and for that I’m thankful.
Currently this month my lockout counter is set at just over 95 failed attempts, and it’s only half way through the month.
Thank-you for the .htaccess fix, my username, (which I’ve gone to great pains to hide), is no longer displayed.
This quote amused me .. “Some experts claim that exposing WordPress usernames is not a security risk.” They’re obviously old school when the login was “admin”, and we had to jump through hoops to change it. My response to the fools is .. IT IS A SECURITY RISK, it’s one step closer to getting inside a WordPress site. [Shakes head in despair.]
The second user name thing didn’t work, ..
Using https://[your website]/wp-json/wp/v2/users/1 produced the output shown below, so I guess that the WordPress programmers sorted that one out.
code “rest_user_cannot_view”
message “Sorry, you are not allowed to list users.”
data
status 401
All in all: I actually feel one step closer to keeping the scum-bag hackers out, many thanks for the tutorial.
RGDS – Terry.
Thanks for this, amazed that people have the time hack so much
As usual, a too-technical-to-understand instruction on how to solve a problem. I don’t have a clue how to open the hidden htaccess and all the other stuff here. But that’s okay, I’ll just pay my developer $100/hour to do it.
You can access your .htaccess file by going to your file manager in cPanel and finding it in your root directory. Hope this helps!
You may have to enable a setting that allows you to see .htaccess or hidden files. The dot in the filename means it is hidden.
– Mia
Bhagwad,
I would think an easier workaround would be to shift all content to a user with non-admin rights. That way, when they discover the username, it is useless to them.
I only suggest this because you make the point that despite your original solution, another method using json became available. (though perhaps I’m misunderstanding your post). Seems like it’s impossible to beat hackers because they are always finding the next technique and all the mods we have to do start to get pretty confusing. BUT, I’d be interested in whether you agree with this?
For sure. I’d say that security has multiple layers. Choosing a good password, trying to prevent hackers from getting info, and of course, reducing the impact of the damage even if they DO get in.
It’s one of the reasons why Linux admins almost never work with the root login – often disabling it altogether. So yeah, you have a good point!
What’s method 3?
Because neither of these work for my site (I have wordfence) but someone just tried using my 2 user names.
I have just tried your method #1 with the .htacess files. Unfortunately, in the newest WordPress version this doesn’t seem to work anymore…
Do I have to set this file anywhere else then the root directory of the blog?
Confirming these methods work by adding them as custom functions with WordPress 5.4 as on August 2020
Hey mate!
Thanks very much for this excellent tip. Very much appreciated.
Cheers
Chris
Hey mate,
I have started to get notifications recently that someone tried to reset my WordPress password. I was wondering how that could be.
I have just implemented your method #1 and it works fine, so one vulnerability less.
Thanks a lot.
Andreas
Thank you, I really appreciate you sharing your knowledge. My Site has been hit a lot lately, I have a strong password but I keep trying to find out how they where getting the username, Thanks to you I made the necessary changes to my site.
did not work for me with author=\d only.
had to change that to:
RewriteCond %{QUERY_STRING} author=([0-9]*)$
RewriteRule ^ \? [L,R=301]
Just want to ad a tip on top of this excellent help. I.m using aiowps for protection and hiding login page and all you can think of, it doesn’t respond at the ?author=1 thing. But anyhow someone had manage to figure out my login page and also username. I found out that in order to complete hide the login page you must turn off the XMLRPC functionality, this is bad news if you use Jetpack. And a good tip for the user name, regardless of this rule in .htaccess they will find your username by just opening a post and click the author of the post, the username of the author will be displayed in the address field. So DON’T use your admin account when writing posts. I’m sure a lot of people know this before me but I did not think of this until now.
Have a nice day and rock on
On the JSON REST Endpoints could it be routed to the 404 page instead of a text link look?
Excellent tip. I wasn’t sure how bots were finding very obscure usernames to try and brute force our login pages. Thanks for the .htaccess edit!
Has anyone had any success with the .htaccess edits on WordPress Multisite?
Not me
THANK YOU VERY MUCH FOR THIS POST!
Hi,
Good day! Thank you so much for this post.
I learned a lot. I tried this and it worked.
But I discovered that the username is still going to be exposed when you use cUrl.
I even tried adding the redirect at the nginx level but it is still exposed via cUrl.
have you encountered this?
Thanks again!
Did not work for me at all. Could the other plugin be interfering?
Here is what htaccess looks like after the WordPress.
…………………
# END WordPress
# BEGIN DS-XML-RPC-API
# The directives (lines) between “BEGIN DS-XML-RPC-API” and “END DS-XML-RPC-API” are
# dynamically generated, and should only be modified via WordPress filters.
# Any changes to the directives between these markers will be overwritten.
order deny,allow
deny from all
# END DS-XML-RPC-API
RewriteEngine On
RewriteCond %{REQUEST_URI} !^/wp-admin [NC]
RewriteCond %{QUERY_STRING} author=\d
RewriteRule ^ /? [L,R=301]
Why is “Code Snippet to WordPress” slightly more inefficient than the .htaccess method?
Because with the code snippet, the server has to execute PHP code, with all the attendant infrastructure. With .htaccess, the server rejects the request very fast.
Using Method 2: Using WordPress JSON REST Endpoints via Fix: Disable via Code …
am I correct in assuming the file you are adding the simple code snippet is wp-json?
If this is the case, my installation of WP does not have such a file.
Where do I add this code?
No, you need to add the code to functions.php. I’ve written a tutorial on how to add code to WordPress. Here it is: https://www.wp-tweaks.com/wordpress-code-snippets-tutorial/ .
Hope that helps!
Probably a silly question (but I am bit of a novice), if I change the permalinks setting from the default one to a more userfriendly form, the username gets exposed in every url pointing to the author archive. I cannot find a way to make wordpress omit the author in messages, or omit the link behind it. Am I overlooking something obvious ?
You don’t need to do all thing above.
I usually use the “admin” as the default username, 1st user.
Then after logged into the Dashboard, I create an other account and set it as the Supper Admin.
The I logged out and login to 2nd account just created and set the admin account to subscriber level.
Let they try to hack the admin account with is only subscriber permission.
Then I use Wordfence plugin, there is an option that block any one try to login as the admin.
Anyone tried to attack the 1st user admin (subscriber level only) will get blocked
That’s all
Thanks for this! I’ve been using “Fix 1: Modifying .htaccess” with success for a couple of years now.
But I recently started writing for someone else’s WP-site when I noticed the following.
I first checked whether they thought of this hack, but apparently they didn’t (I could access all usernames by incrementing the number /?author=2, /?author=3, 4, etcetera).
But then I realized that every blogpost also showed the name of the author. Clicking on the name shows “the author’s page” i.e all posts by that author (there are a bunch of people who write posts for this website).
When I got my user account for this WordPress-website, I added a nickname and selected it as my display name. Profile setting: “Display name publicly as” > [my nickname]. This way my nickname is shown with posts written by me. But now, when I click on it, I goes to:
www.website.com/author/USERNAME (And NOT: www.website.com/author/nickname)
So my username is exposed like this anyway! Is there a way around this? Is this a generic WP thing or perhaps Theme specific?
I prefer to just disable the author pages entirely!
That would probably be the easiest way to tackle this. Will suggest this to the admin of the site. Thanks for the swift reply! Cheers!
That would probably be the easiest way to tackle this. Will suggest this to the admin of the site. Thanks for the swift reply! Cheers!
That would probably be the easiest way to tackle this. Will suggest this to the admin of the site. Thanks for the swift reply! Cheers!
Hello, I’m using Code Snippets plugin for WordPress. Method 1 code works perfectly. For some reason, the JSON Endpoint code is not blocking. I saw some else posted using Code Snippets and I’m assuming his is working. Am I missing something? I create a blank snippet, then add:
function disable_rest_endpoints ( $endpoints ) {
if ( isset( $endpoints[‘/wp/v2/users’] ) ) {
unset( $endpoints[‘/wp/v2/users’] );
}
if ( isset( $endpoints[‘/wp/v2/users/(?P[\d]+)’] ) ) {
unset( $endpoints[‘/wp/v2/users/(?P[\d]+)’] );
}
return $endpoints;
}
add_filter( ‘rest_endpoints’, ‘disable_rest_endpoints’);
Save & Activate. Then I’m assuming it should work, but it does not. What’s the best way to troubleshoot this?
good post. thank you for the information about how a user name is exposed, and the .htaccess code to disable that exposure.
I just implemented it on 2 sites that seemed to be under intense login attacks even though I had 2-step verification and would change the passwords often. I would even take the (drastic) steps to create a new administrative user(name), reassign all my posts to that new user, and then delete the old user, only to find that the next day the hackers were attempting to login with my new user name!
after using your .htaccess suggestion, and creating a new user/deleting old user, the attacks have been reduced dramatically, and none of the login attempts have been with the new user name – they continue to try the old name(s) and of course the ubiquitous ‘admin’ as a user name. Thanks again.
You’re welcome! I’m glad you found it useful 🙂
Can I also disable the WordPress Rest Endpoint JSON with a Woocommerce installation without any problems
Hello. I did this but page 404 appears? Is it possible to tell me what to do to redirect you to the main page of the site?
Hello there,
I used as following on the function.php and working just fine for multiple websites(remember,if you change the site theme tis need to be done again):
function disable_rest_endpoints ( $endpoints ) {
if ( isset( $endpoints[‘/wp/v2/users’] ) ) {
unset( $endpoints[‘/wp/v2/users’] );
}
if ( isset( $endpoints[‘/wp/v2/users/(?P[\d]+)’] ) ) {
unset( $endpoints[‘/wp/v2/users/(?P[\d]+)’] );
}
return $endpoints;
}
add_filter( ‘rest_endpoints’, ‘disable_rest_endpoints’);
// block WP enum scans
// https://m0n.co/enum
if (!is_admin()) {
// default URL format
if (preg_match(‘/author=([0-9]*)/i’, $_SERVER[‘QUERY_STRING’])) die();
add_filter(‘redirect_canonical’, ‘shapeSpace_check_enum’, 10, 2);
}
function shapeSpace_check_enum($redirect, $request) {
// permalink URL format
if (preg_match(‘/\?author=([0-9]*)(\/*)/i’, $request)) die();
else return $redirect;
}
I made the .htaccess edits as shown, but when I tested my site it appeared not to work.
I now know that this is because my Chrome browser was using cached data.
Works perfectly on the latest version of WordPress, 6.02, and exactly as described for both types of hack.
The Custom Plugin was a bonus to gather together all the odds and sods I use on different websites – so easy to use with the WordPress edit plugin feature.
Many Thanks for the heads up as I’d also wondered why hackers knew my username straight after I’d just changed it.
This website looks so useful I think you need a better indexing system. I initially googled your articles on the mobile and had 3 posts open as I made sense of the info and everyone’s informative comments. I then moved to the desktop to implement things on one of my sites and struggled to locate the original post. Your search box at the bottom of the page worked great but I’m feeling there is a huge amount of useful stuff on here which I can’t see!
Hope that’s not too much of a whinge especially as this was a well written article with links to another 2 making the whole process pain-free. Nice to see bloat free code here too. Well done!
PS I guess I’ll need to change my username again in case the hackers keep that sort of info….
I still found your username is: bhagwad
/wp-json/wp/v2/users/1
Why don’t you hide it?
Just added the code snippets to a plug in file as suggested and working perfectly. Many thanks. I was getting so many spam login attempts, it was quite concerning. I find it remarkable that WordPress don’t consider allowing easy access to user names as a security issue…… Anyway, you are a star!!
I have written a detailed wordpress security tweaks blog post, anyone can check and inform me to update the post as per your experience.
In this post, for the .htaccess code option, the screenshot of the code inserted in the file is missing a line listed in the snippet. Assume that’s a error?
RewriteCond %{REQUEST_URI} !^/wp-admin [NC]
If word press is up to date, does the two methods mentions still show the vulnerabilities?
THANK YOU SO MUCH!
I couldn’t make sense as to how hackers were finding my usernames and trying to log in.
I was using IPlocation blockers to limit the attempts, but this has help so much.
Thank you for the info! This worked like a charm!