Sometimes, Cloudflare blocks REST API requests and prevents WordPress from working correctly. I most commonly encounter this problem when the WordPress Gutenberg editor throws the following message:
Updating failed. The response is not a valid JSON response.
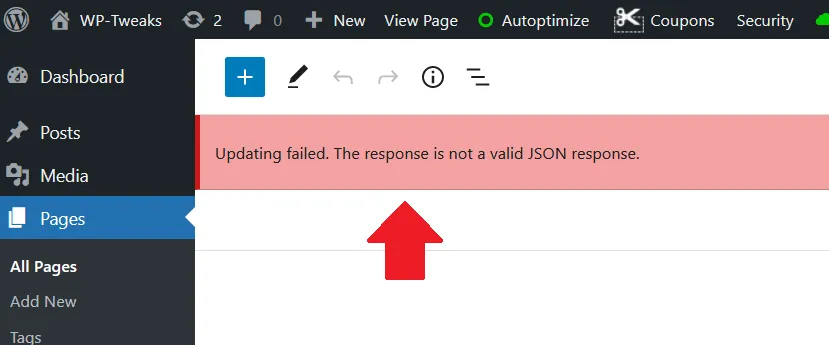
Here’s what you can do to fix this problem.
Table of Contents
Methods to Stop Cloudflare from Blocking REST API Requests
I’ve listed these methods in order of surgical to nuclear.
1. Disable the Specific WAF Rule that’s Blocking the REST API
Cloudflare’s Web Application Firewall (WAF) is a set of managed rules that block all kinds of threats. Sometimes, though, it blocks things it shouldn’t. First, we need to see why Cloudflare blocked any particular response. To do this, go to “Security -> Overview” from the Cloudflare dashboard:
Scroll down to the “Activity Log” section. You will find a list of all security events, including all blocked requests. Find the one that matches the blocked REST API request you’re interested in. You can identify this by identifying your IP address or country in the list. For the above example of blocking the REST API from Gutenberg, here’s a screenshot of the detailed security event:
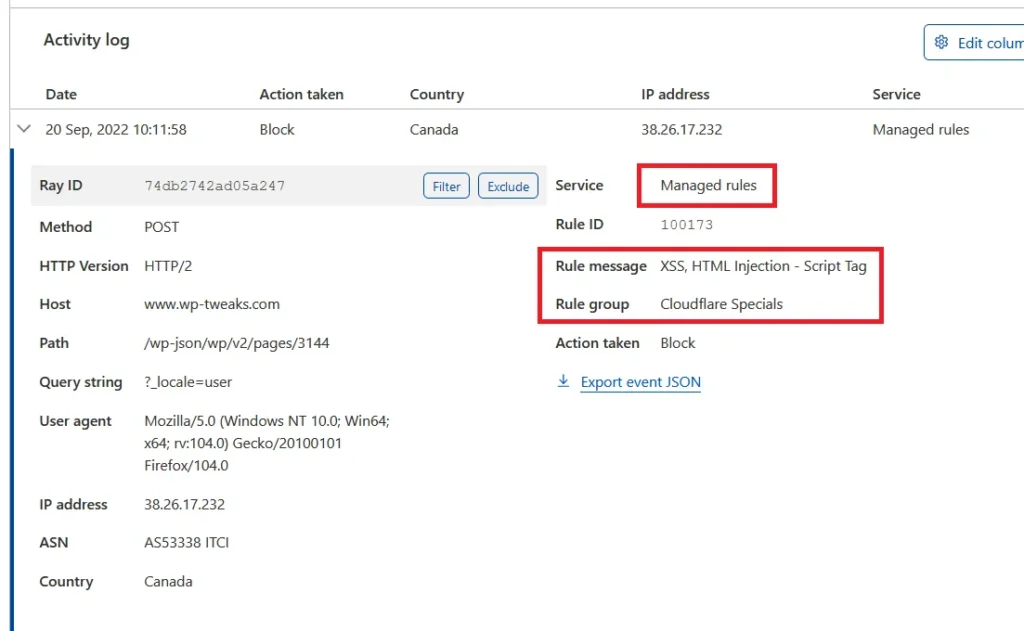
In the above screenshot, the REST API request was blocked by “Managed Rules”, which is Cloudflare’s WAF. The specific rule group is “Cloudflare Specials”. To fix this, we need to disable the Cloudflare Specials rule group – at least when editing Gutenberg.
Go to Security -> WAF in the dashboard, and then select the “Managed Rules” tab. Scroll down till you find the rule group as in the screenshot, and turn it off as shown here:

Give the system a few minutes to be safe, and try again. If the WAF was blocking the REST API, it should work fine now.
2. Disable Super Bot Fight Mode
Apart from the WAF, Cloudflare has a tool that blocks bots. Both free and paid customers can use this tool, and it can block the REST API that WordPress needs to function. If the bot fight tool was responsible, you’ll see the description in the security event with the Ruleset Name: “Bot Fight Mode for Definite Bots”.
If the bot fight mode is the problem, go to “Security -> Bots” and turn it off. For the Cloudflare free tier, this should be a simple switch. For Pro accounts and higher, click “Configure Super Bot Fight Mode” and set the “Definitely automated” traffic to “Allow” like this:
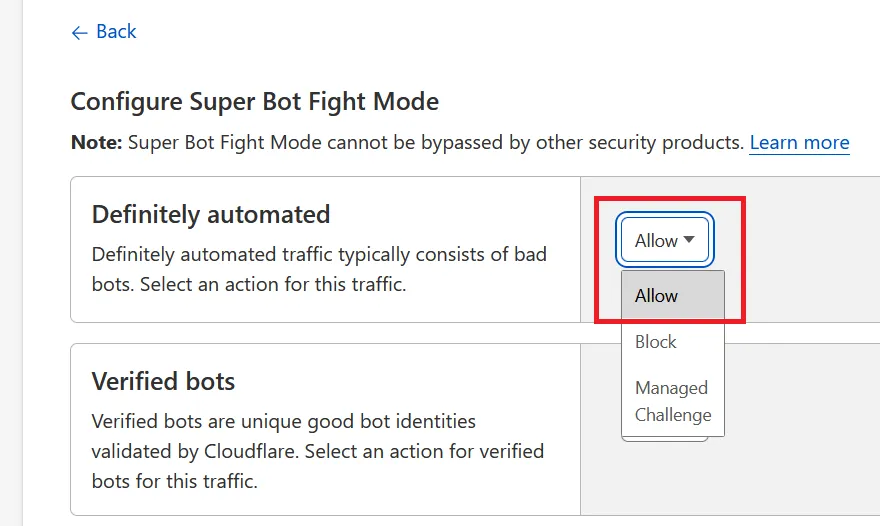
Once more, give it a minute for the system to process your changes, and try again. If the bot fight tool was blocking the REST API, it should allow further requests.
3. Disable the Cache Deception Armor Page Rule
In 2018, Cloudflare released a new page rule called “Cache Deception Armor”, which involves a complicated attack tricking reverse-proxies like Cloudflare into caching content that they shouldn’t.
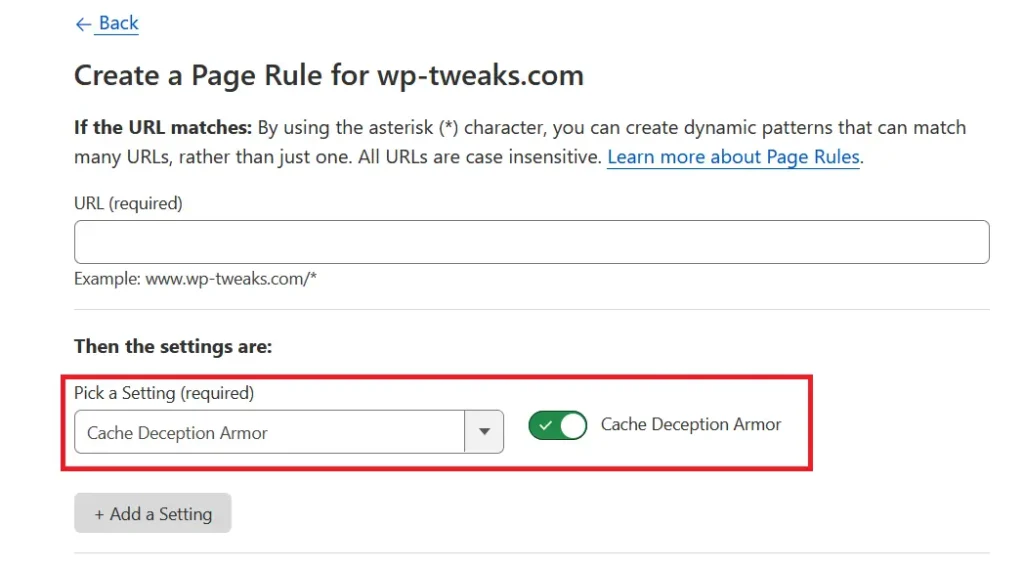
The attack details aren’t important, but this page rule can cause strange interactions and could be why Cloudflare is blocking your REST API request. If you’re using the Cache Deception Armor page rule, you should try disabling it and see if it fixes the problem.
4. Check your Firewall Rules Blocking JSON Requests
Sometimes we create overly restrictive firewall rules in Cloudflare that can block REST API requests without intending to. For example, I wrote a post explaining how hackers can find your WordPress username, and one of the methods was using JSON REST API endpoints. I use Cloudflare firewall rules to block JSON requests as shown here:
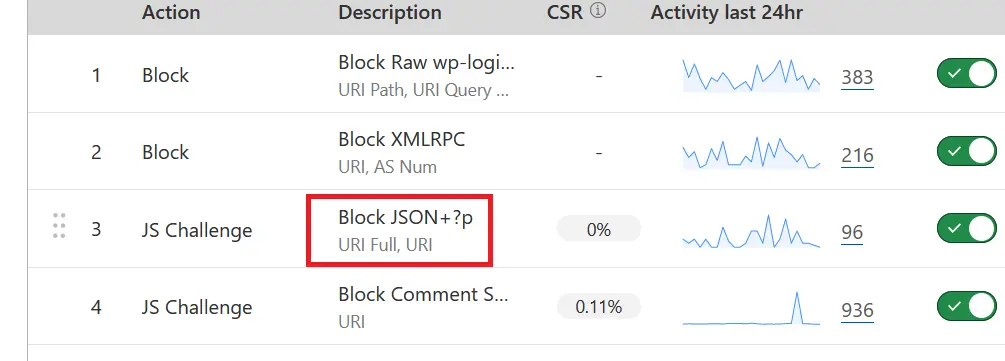
The problem is that the REST API relies on these JSON requests, so if you block these URLs, then an application like WordPress can’t function correctly. I work around this by requiring a JS challenge for all PHP pages, so by the time I use Gutenberg, I’m already verified, and Cloudflare doesn’t block my REST API requests with a 2-hour timeout.
So be careful while setting your firewall rules. If you make them too restrictive, Cloudflare can easily block legitimate REST API calls.
Disabling Security via Cloudflare Page Rules Doesn’t Work
One solution that DOESN’T work is disabling Cloudflare security via page rules. This is because this blocks neither the bot fight mode, the WAF, nor the firewall rules. Here’s a list of services the Cloudflare page rules disable:
- Email obfuscation
- Rate limiting (older version)
- Scrape shield
- Server side excludes
- URL and Zone lockdown
- WAF rules (old version)
Note that you can’t disable the new WAF rules or bot fight mode via page rules. So, allowing REST API requests by disabling the Cloudflare security won’t work.
Temporarily Disable Specific Cloudflare Rules
I find Cloudflare’s WAF and bot fight mode so valuable that I don’t disable them permanently. Cloudflare blocking REST API requests only impacts me while using the Gutenberg editor in WordPress since I don’t use the Jetpack plugin. So I disable the specific Cloudflare rules that affect my workflow and re-enable them after I finish. Using Cloudflare firewall rules to block WordPress spam is very effective. To be sure, I open Cloudflare in a separate browser window, so I don’t accidentally close it with the other tabs. When my work is done, I see the other window open, and I remember to re-enable the relevant rules. I suggest you do the same.
Use Cloudflare Zero Trust for More Foolproof Protection
If you find that protecting your login pages is too complicated using firewall rules, then consider using the free Cloudflare Zero Trust tool to achieve the same thing. Instead of checking the validity of each visitor to a sensitive area of your application, you authorize Cloudflare to allow only those who have access to a set of e-mail IDs. Cloudflare then sends an OTP to anyone with a whitelisted e-mail and only when the OTP has been confirmed, can a user proceed to a certain page.
With Cloudflare Zero Trust, you have tighter control over who can access your application.

Speak Your Mind